DASCTF WriteUP
DASCTF2024最后一战 WriteUP
排名
89 名
解题思路
CHECKIN
签到题
打开题目后给了一个网址https://game.gcsis.cn,根据提示使用dirsearch进行扫描,扫出目录下的robots.txt
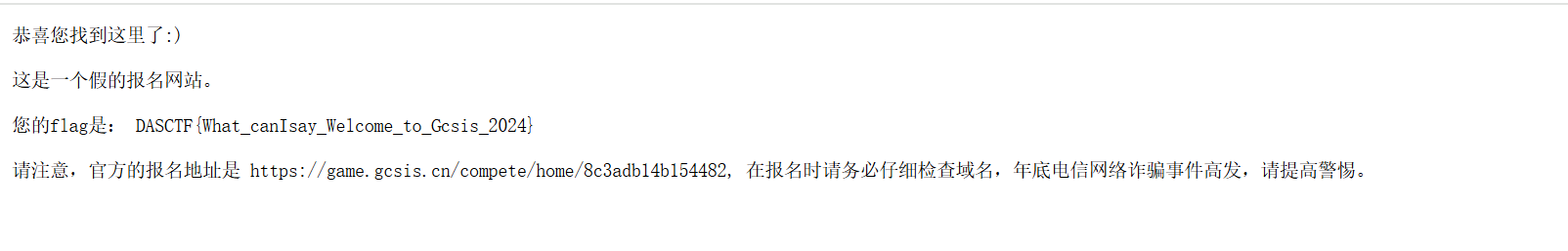
访问后得到flag
REVERSE
tryre
首先用exeinfo看一下有没有壳
发现没壳,用ida打开直接转换成伪代码
然后发现里面有个类似base64表的东西ZYXABCDEFGHIJKLMNOPQRSTUVWzyxabcdefghijklmnopqrstuvw0123456789+/
查看main,发现类似base64操作和xor操作
让GPT生成下代码
def custom_base64_decode(encoded): decode_table = "ZYXABCDEFGHIJKLMNOPQRSTUVWzyxabcdefghijklmnopqrstuvw0123456789+/" base64_table = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" # 创建解码映射 trans = str.maketrans(decode_table, base64_table) # 转换为标准base64字符 standard_base64 = encoded.translate(trans) # 解码过程 from base64 import b64decode try: return b64decode(standard_base64) except: return None def solve_flag(): target = "M@ASL3MF`uL3ICT2IhUgKSD2IeDsICH7Hd26HhQgKSQhNCX7TVL3UFMeHi2?" xored = ''.join(chr(ord(c) ^ 2) for c in target) flag = custom_base64_decode(xored) if flag: return flag.decode('ascii') return "解码失败" def main(): print("[*] Starting flag solver...") print("[*] Target encoded string: M@ASL3MF`uL3ICT2IhUgKSD2IeDsICH7Hd26HhQgKSQhNCX7TVL3UFMeHi2?") flag = solve_flag() print(f"[+] Recovered flag: {flag}") # 验证长度 if len(flag) == 44: print("[+] Length verification passed (44 characters)") else: print(f"[-] Warning: Flag length is {len(flag)}, expected 44") if __name__ == "__main__": main()解得flag: DASCTF{454646fa-2462-4392-82ea-5f809ad5ddc2}
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 QingChenyou | Luda' Blog!
